arp poisoning within LAN (usually a client infected with a virus/Trojan and it spoof the default router mac addr and take the network down or by ddos the default router with arp) is one of attack that is a bit difficult to defense. Subnetting the network into much more smaller part can reduce the impact of it. ie., separating your servers from your clients. However, there’s no protection between clients and once the default router mac addr is poisoned in the client subnet, the subnet housed those clients is still down. Moreover, resubnetting the network involves high hidden management costs as well. The other method is that one can deploy switches with anti-arp poisoning feature (Cisco 35XX switch or above with DHCP snooping and arp inspection). This providescomplete protection but involving replacement of a no. of edge switches. Moreover, those clients must be using DHCP to make it work (or you need to enter their mac addr manually into the switch…)
Another much cheaper method is to segment your LAN into two parts. One is a trusted zone where ur router, servers and clients you would like to be separated from others (say your admin machine) are placed. The other is an untrusted zone where your clients will be placed. These two segments will be connected using a Linux bridge. arp reply/request will be allowed from the trusted to untrusted zone but on the other direction they will be inspected and only reply from registered pair of ip/mac are allowed.
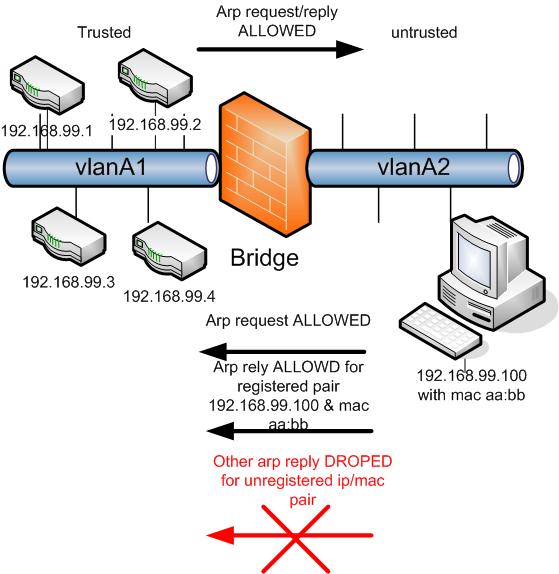 This can be easily accomplished in a Linux bridge using ebtables:
This can be easily accomplished in a Linux bridge using ebtables:
#!/bin/bash #eth0 : connected to vlanA1 (trusted) #eth1 : connected to vlanA2 (untrusted) PATH="/usr/local/sbin" ebtables -F ebtables -X #allow arp reply of below pair only from eth1 ebtables -A FORWARD -i eth1 -p arp --arp-ip-src 192.168.99.100--arp-mac-src aa:bb:cc -j ACCEPT #allow arp request from eth1 ebtables -A FORWARD -i eth1 -p arp --arp-opcode 1 -j ACCEPT #drop all other arp reply from eth1 ebtables -A FORWARD -i eth1 -p arp -j DROP




















Look forwarding to deploy it in our network. So what network segment should we deploy it first as a pilot site?
oc this should be used to protect our upstream router interface first
Большое спасибо за объяснение, теперь я буду знать.
Добро пожаловать
LINUX bridge is a way to connect two Ethernet segments together in a protocol independent way.Packets are forwarded based on Ethernet address, rather than IP address (like a router). Since forwarding is done at Layer 2, all protocols can go transparently through a bridge.