IERG4210 (Spring 2021)
Course Overview and Basic Concepts
Sherman Chow
Course Overview
Teaching Team
- Instructor
- Prof. Sherman Chow
- Office: SHB808
- Office Hour: appointment via email
- Zoom or MS Teams
- Email: [login]@ie.cuhk.edu.hk
- Prepend your email subject with [IERG4210]
- Use your institutional email account
- Risk sending your email to my junk box
- (and I will hardly read that)
About Me
- Cryptographer
- Applied Cryptography
- Distributed System Security
- Privacy-Enhancing Technologies
- Privacy-Preserving Big Data Analytics
- My Path
- BEng in Computer Engineering (HKU)
- MPhil in Computer Science (HKU)
- PhD in Computer Science (NYU)
- Post-doc in Combinatorics and Optimization (UWaterloo)
Tutors
- MUI Hong Yin
- PhD Year 1, Cantonese
- XIE Siyue
- PhD Year 2, Cantonese/Mandarin
- ZHENG Yu
- PhD Year 3, Mandarin, Past TA
- ZHOU Yutong
- PhD Year 2, Mandarin, Past TA
- All except Xie (SHB803)'s office is SHB726
- Office hour:
- To be announced through eLearning system later
Course Description
- Web Programming
- The programming language for both client and server sides
- Optimization and performance issues
- Tools for app. development, e.g., version management, etc.
- Security
- Security design principles
- Common vulnerabilities
- Basic hacking and penetration testing techniques
- Practice
- Acquire the skills through the whole development cycle
Topics to be Covered (1)
- Web Architecture
- HTTP, URL, etc.
- Explains how a web app is loaded
- Web Dev. Languages
- HTML, CSS, JavaScript, PHP, and SQL
Topics to be Covered (2)
- Web Development Components
- User Interface Design
- both client and server sides
- Forms Handling
- both client and server sides
- Web and Database Server Management
- Session Management & Authentication
- Explains: how a web app can be developed
- User Interface Design
Topics to be Covered (3)
- Web App. Security
- 8 Security Principles
- Security Goals
- Basic Concepts: CIA Triangle
- Other issues: Authentication, Non-repudiation, etc.
- Browser Security Model: Same Origin Policy
- Cross-origin Communication (e.g., to support mashup apps.)
- OWASP Top 10 application security risks
- Explain: how a web app can be secured
Topics to be Covered (4)
- Browser Security
- SSL, Certificate, Side-Channel attack, Phising, DNS attacks, etc.
- Performance and Optimization
- Settings and Code Tweaks
- To make your web site run faster
- Search Engine Optimizations
- To make your web site appear first in search results
- Settings and Code Tweaks
- Code testing and Penetration test of web applications
- Testing for security vulnerabilities (instead of functionalities)
Tentative Teaching Schedule
- See the course home page for the past edition as a reference:
- http://course.ie.cuhk.edu.hk/~ierg4210
- Thanks to the teaching material from Prof. Kehuan Zhang
- (who was "bootstrapped" by Dr. Adnois Fung (our IE alumnus) who made this course happen once upon a time)
- Meanwhile, we will keep updating the current edition:
- Could be adjusted a bit according to actual teaching & learning progress
Learning Activities
- Weekly Lectures
- Readings
- Some book chapters/pages (30 min)
- To reinforce your leaning
- Tutorials
- Assignment guidance
- Review on important topics
- Assignments
- Web development and Hacking (7 × 7 Hours)
- Learning through practicing
- Getting Help
- Office hour/ Tutorial Time/ By appointment / Class break / email
- Piazza group (to be set up)
The Use of Piazza
- Functionalities
- Course bulletin
- Sample code release
- Online Q&A
- Peer support
- You are encouraged to
- Post your questions on Piazza
- Ask for help from peers and TAs
- Engage in the discussion of others' issues
- The top 10% most active students in answering questions, supporting other students, etc., will be given 5 bonus points for their final grade
Learning Outcomes
- Demonstrate understanding of the principles and techniques in the design and development of secure web applications
- How to build a workable web site
- How to make the web site secure
- Others: performance, search engine optimization, etc.
- Special topics (if time permits)
Grading and Evaluation
- Assignments 40%
- Middle Term Exam 20%
- Final Exam 40%
(Lots of) Assignments, ALL are hands-on
- HTML and CSS
- Form Handling and Image Upload
- Authentication
- AJAX Shopping List
- Payment Gateway Integration
- Free-style Features: Password Reset/Mashup
- Vulnerability Discovery and Peer-hacking
Assignment Theme: An Online Store
- To provide you with chances to code and practice what you learnt
- An e-commerce website deserves protection (for $) far more directly than many other examples.
- Although source code for shopping carts is well-known everywhere (books/web), it may not be secure.
- 6 phases (and deadlines, approx. bi-weekly) towards a final product
- Final product: a shopping website prototype (e.g.: parknshop.com)
- TAs will track students' progress
- Invite weaker students to attend an interim demo, which is compulsory for students lagged behind in first 4 phases
- To ensure students are capable of completing the basics
- To forfeit the penalty of late submissions
- The 7th phase will be peer-hacking
An Example View on Assignments
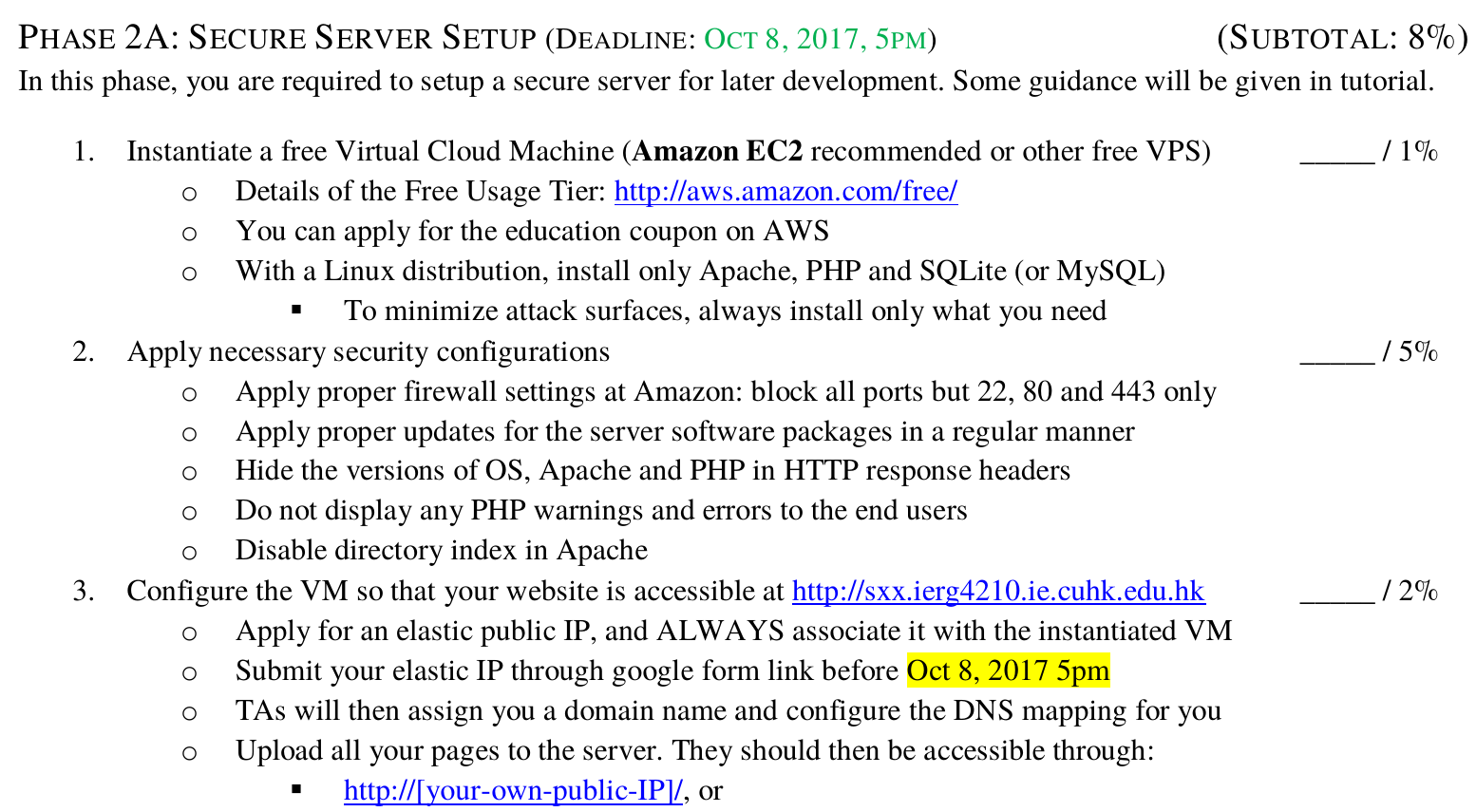
More About Assignments
- Prepare a credit card (debit card?)
- To apply for a free Amazon EC2 cloud instance
- It is free for about one year
- (be careful to not use extra services and features!)
- Let us know if you have any trouble
- To apply for a free Amazon EC2 cloud instance
- Submit all related codes to elearning before the deadline of each phase
- DO NOT COPY, or we will catch you during the live-demo session
- TAs will not debug code for you
- Seeking peer helps if possible, e.g., those talented coders
- Post your questions on Piazza
- Attend tutorials to make sure you have mastered the knowledge (some tutorials are helpful for assignments)
Grading
- Final demo: all students will be graded at the end of semester
- 0% - 100% Result-oriented
- Based on completion of the required features
- No restrictions on the use of languages/libraries
- (Ruby and jQuery? fine! as long as you can learn it by yourself)
- -75% Challenge-response Q&A
- Be challenged in person on your understanding of code
- Marks to be deducted if coded something you don't understand
- Code Cross checking with previous submissions!
- To prevent code copying and reuse
Student/Faculty Expectations on Teaching and Learning
http://www.erg.cuhk.edu.hk/upload/StaffStudentExpectations.pdf
Warning!
- IERG4210 is a demanding course
- It requires you to really put some time to it
- Fail rate?
- Depends on students performance
- About 10% for a prior offering
- Missing from final exam/mid-term exam
- Did not finish assignments, etc.
- But at the same, it is a rewarding course
- Helpful for your job
- Or many other places
- Rate for A/A-
- No fixed rate, depends on your performance
Assignments and Project Polices
- Submission Policies for Assignments and Project
- Approximately two weeks of time for each phase
- Early submission reward: 48/24-hour in advance
- Later submission penalty: 10% will be deducted per 24-hour
- Honesty in Academic Work: follow the university policy
- Pay attention to "typical cases" (check the URL below)!
CUHK places very high importance on honesty in academic work submitted by students, and adopts a policy of zero tolerance on cheating in examinations and plagiarism http://www.cuhk.edu.hk/policy/academichonesty
- Ethical Hacking
- You need to learn how to hack, or you don't know how to protect.
- BUT, please apply hacking skills in a LEGAL and ETHICAL ways
Learning Resources
- Textbooks
- N. Daswani, C. Kern, and A. Kesavan, "Foundations of Security: What Every Programmer Needs to Know". 2007
- D. Stuttard, and M. Pinto, "The Web Application Hacker's Handbook: Discovering and Exploiting Security Flaws". 2008
- W. J. Gilmore, "Beginning PHP and MySQL: From Novice to Professional". 2010
- And other online web resources
Class Policy
- Course lectures will be recorded and put on course Web site
- So you can watch it off the lecture hours
- Assignment: follow policies mentioned in previous slide
- Late submission with penalties: (0.9)^n for delay n days
- To be fair for everyone, make evaluation practical and feasible
- WARNING!!
- This is a course that requires you to spend lots of time to learn several new programming langauges (like HTML, CSS, JavaScript, PHP, SQL), as well as many new concepts on Web application security and optimization, so attending lectures (or watching lecture videos) is far from enough.
- So if you would skip many lectures (e.g., Friday mornings'), I would recommend you to take a different course
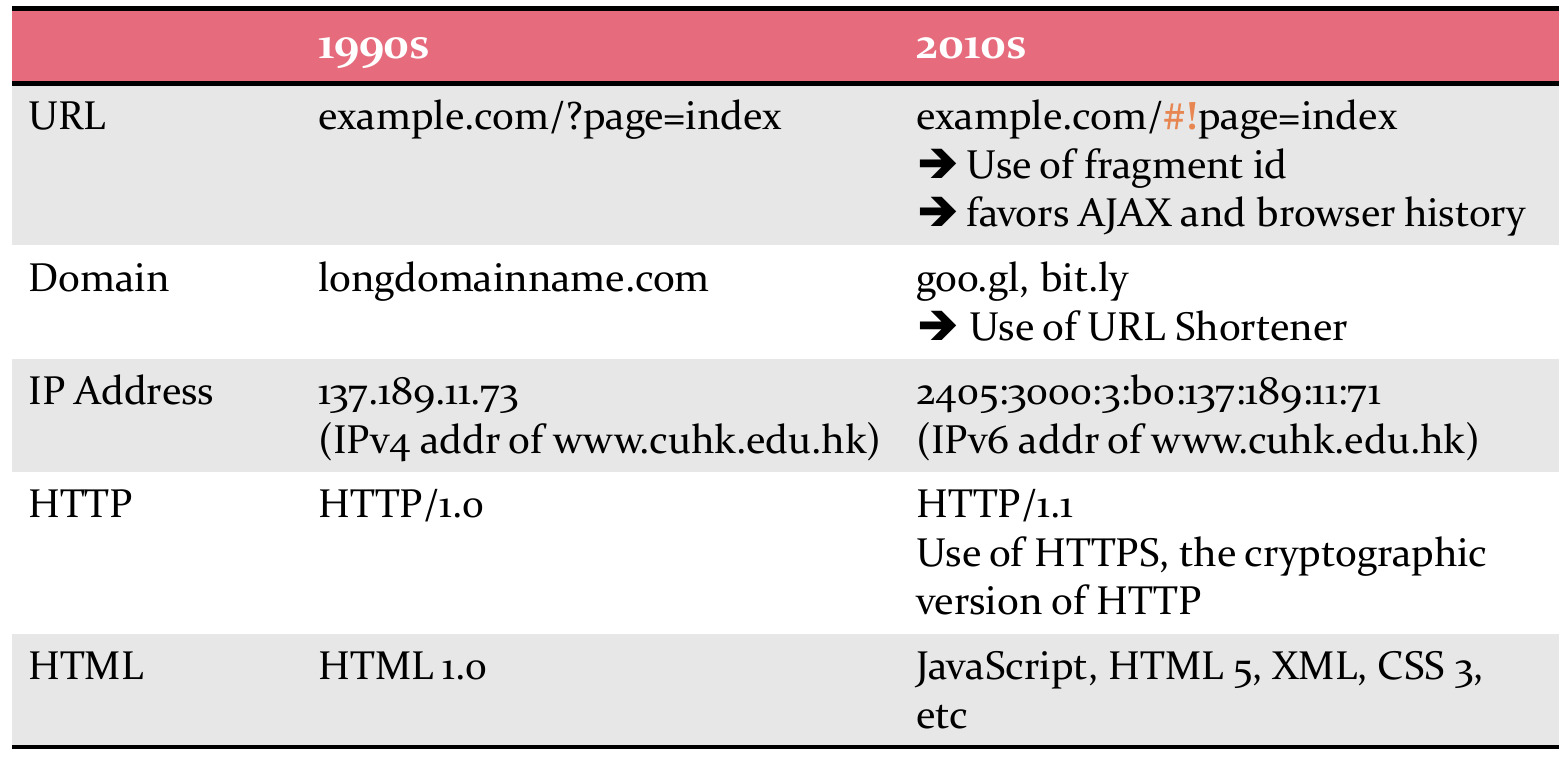
Basic Concepts of Internet
Contents to be mentioned
- Internet Components
- URL
- Domain Name
- IP Address
- World Wide Web
- Evolution of the Web
Journey of Web Browsing
- What is going on once you want to visit a web site?
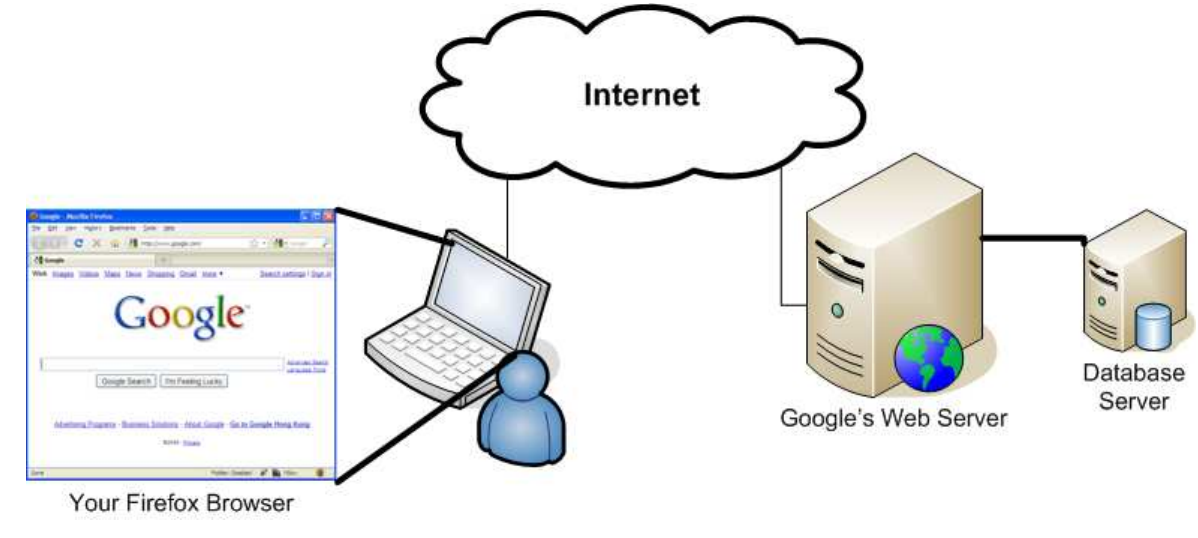
Universal Resource Locator (URL)
- URL is a string that references an Internet resource.
- For example
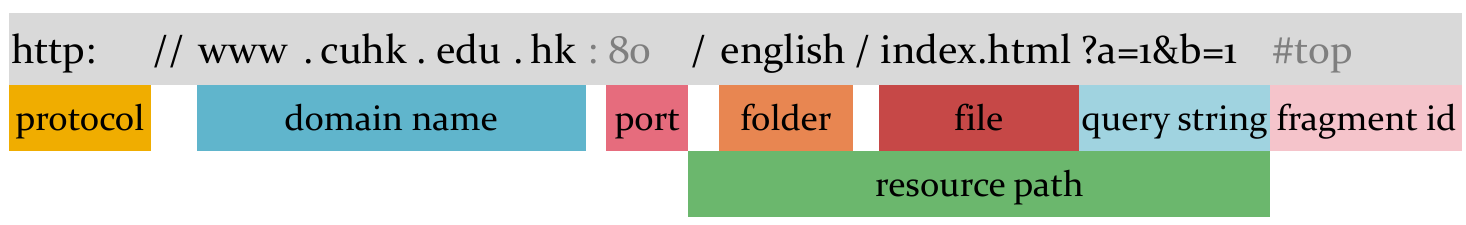
- Port number maybe omitted if the default one is used
- 80 for HTTP, 443 for HTTPS, 21 for FTP, etc.
- Port number maybe omitted if the default one is used
- More examples: Can you tell the component names?
- https://www.ebanking.hsbc.com.hk:443/1/2/logon
- ftp://ftp.cuhk.edu.hk:21
Domain Name
- Domain Name System (DNS) server resolves domain name to IP addresses for ease memorizing, or vise verse
Domain Name Examples

Demo: use dig or nslookup to lookup a domain name
IP Address
- Address is a numerical address that references a device connecting to a computer network using the Internet Protocol.
- Take IERG3831/3841 for more information on routing protocols
- Reference: http://en.wikipedia.org/wiki/IP_address
- Example: how about the DNS record of www.google.com?
- Try to keep querying multiple times ...
- Round-robin DNS: a domain name is resolved to multiple IP address, to be swapped after each query
- Achieving load balancing, often employed by high-traffic websites
- Domain can be one-to-many mapping
Brief History of World Wide Web
- World Wide Web is the point-and-click system of navigating through information shared over the Internet by using hypertext
- Invented by a physicist Tim Berners-Lee at CERN for sharing physics findings
- In 1990, the HyperText Transfer Protocol (HTTP), first HTTP Server and Browser (WorldWideWeb, a HTML renderer) were all born
Founders Chair at MIT
- References:
BUT, they have all evolved ...
Reading Material - How the Browser Works
- https://www.html5rocks.com/en/tutorials/internals/howbrowserswork
- You can also find some other reference materials online
- It is important to know how the browser works in order to better understand CSS/DOM/Performance optimization, etc.
The Evoluation of the Web - Tech. Perspective
- Reference: http://evolutionofweb.appspot.com
Security Principles
Securing the system as a whole for greatest secruity
- Securing the system: prevent, detect, and respond
- as a whole: focusing not on any particular aspect but ALL aspects
- greatest security: usable, fault-tolerable, risk manageable
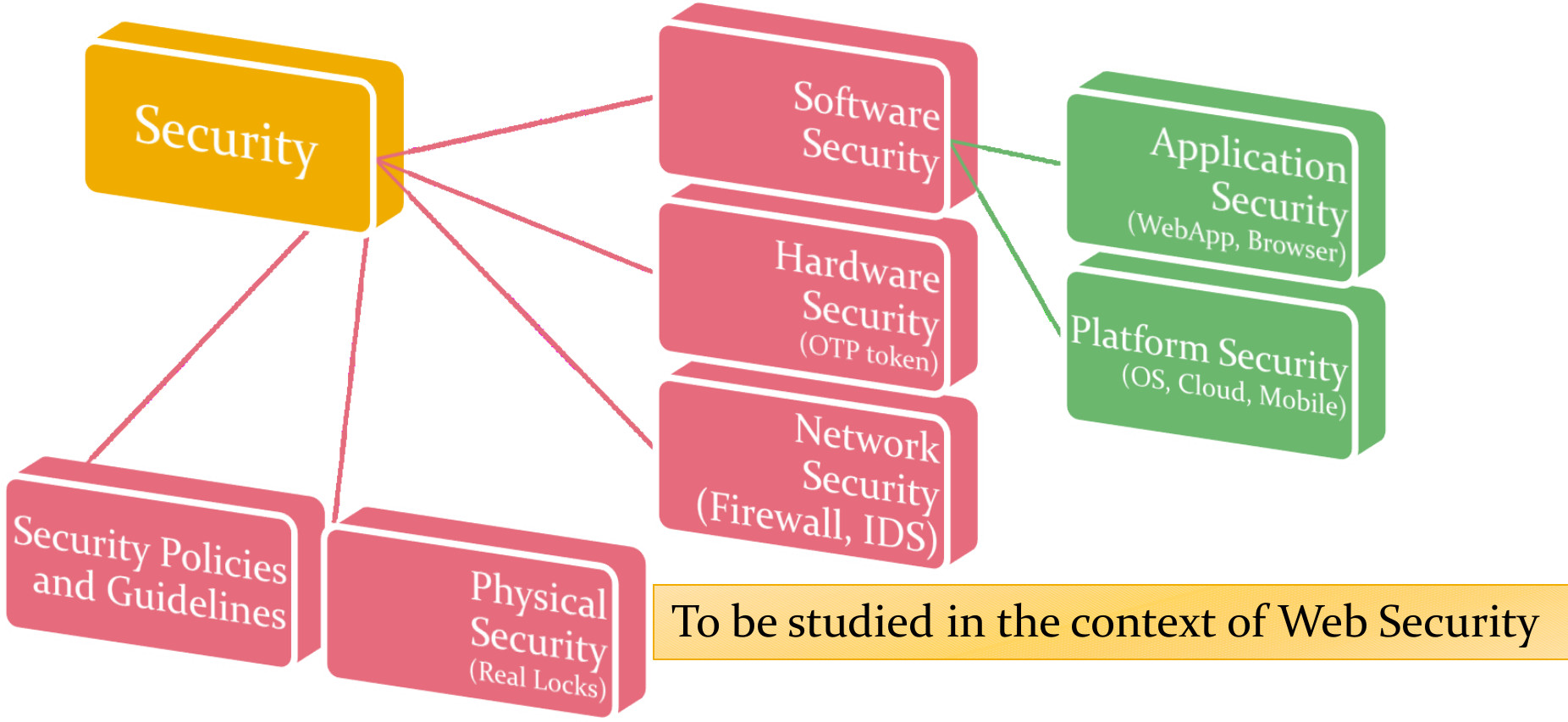
8 Secure Design Principles (p.1/6)
- Securing the Weakest Link
- Security is like a chain; a system is only as strong as its weakest link, which is most likely attacked
- Risk Management Nothing is perfectly secure unfortunately!!
- Start by addressing the most serious risk (weakest) in your list, instead of those that is easiest to mitigate
- Stop until all components are under a manageable level of security
- Examples:
- Attackers often bypass crypto, instead of breaking it
- Un-educated users often click "yes" to everything
8 Secure Design Principles (p.2/6)
- Defense-in-Depth
- Deploy holistic and diverse defense strategies so that even if one fails, the others can hopefully prevent a complete failure
- Layers of defense. Promote redundancy. NO single point-of-failure!
- Examples:
- prevent, detect, contain, and recover
- One-Time Password as 2nd defense if password is stolen
- Secure Failure
- A complex system can unavoidably break down, but it should not revert to insecure behavior
- Promote the use of try/catch blocks in programming
- Examples:
- Disclose sensitive info in error or debugging messages?
- A lift must not fall even if it fails to work
8 Secure Design Principles (p.3/6)
- Least-privilege
- A user or program is granted the minimum amount of privilege (access and time granted) that is just sufficient to complete a task
- Examples:
- Block unneeded port numbers to reduce attack surfaces
- Permissions are restricted even if an app is compromised
- Compartmentalization / Separation of Privilege
- Break the system up into as many isolated units as possible to minimize potential damage
- Examples:
- Run a forum on a server that stores credit card numbers?
- Sandboxing tasks to run with its own privileges
8 Secure Design Principles (p.4/6)
- Simplicity
- KISS (Keep it simple, stupid!): Keep a system design and implementation as clean and straightforward as possible
- Reuse Off-the-shelf libraries whenever possible to stay simple
- "Security by Obscurity" is not secure --> reverse engineering
- Crypto is secure not by hiding its algorithm but only a secret key
- Example: complex system is always hard to maintain and analyze
- KISS (Keep it simple, stupid!): Keep a system design and implementation as clean and straightforward as possible
8 Secure Design Principles (p.5/6)
- Simplicity
- Usability: Design an idiot-proof and usable system as users
- are lazy,
- never read manual,
- and ignore security if given a choice.
- Considerations on trade-off security with convenience
- Example: "You are going to lose money?" Uses click "yes" to everything.
- Secure Defaults: Deploy applications that are with more secure configurations by default. Let advanced users to relax them.
- Example: Firewall should be defaulted to deny all traffic
- Usability: Design an idiot-proof and usable system as users
8 Secure Design Principles (p.6/6)
- Promote Privacy
- Privacy to be collected and used fairly as agreed by users (FB?)
- A system should keep users' sensitive information confidential
- Example: Stealing credit card numbers and IDs from insecure database
- Don't extend trust easily. Be skeptical!
- Be reluctant to trust your clients, who may not use a system as intended. (i.e. always validate and sanitize user inputs, one of the key problems for web application security)
- Be reluctant to trust external components, which may not be built by security experts
- Be reluctant to trust yourself, who may think what you built is perfect
Reference: IBM developerWorks, "Software Security Principles by G. McGraw, and J Viega", Oct 1st, 200.
Information Security Goals
- CIA Core Goals: Confidentiality, Integrity and Availability
- Confidentiality and Integrity depends on Authentication and Authorization
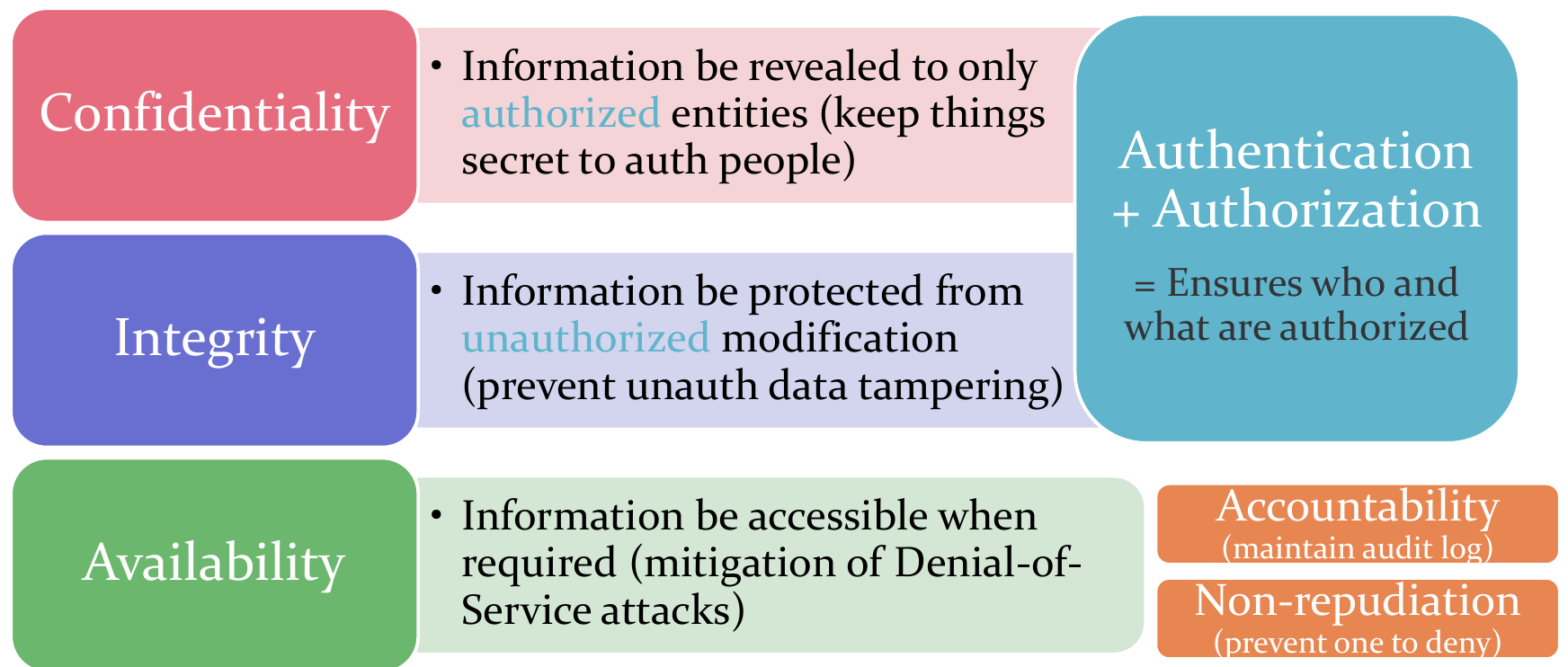
- Mainly covered in couse IERG4130
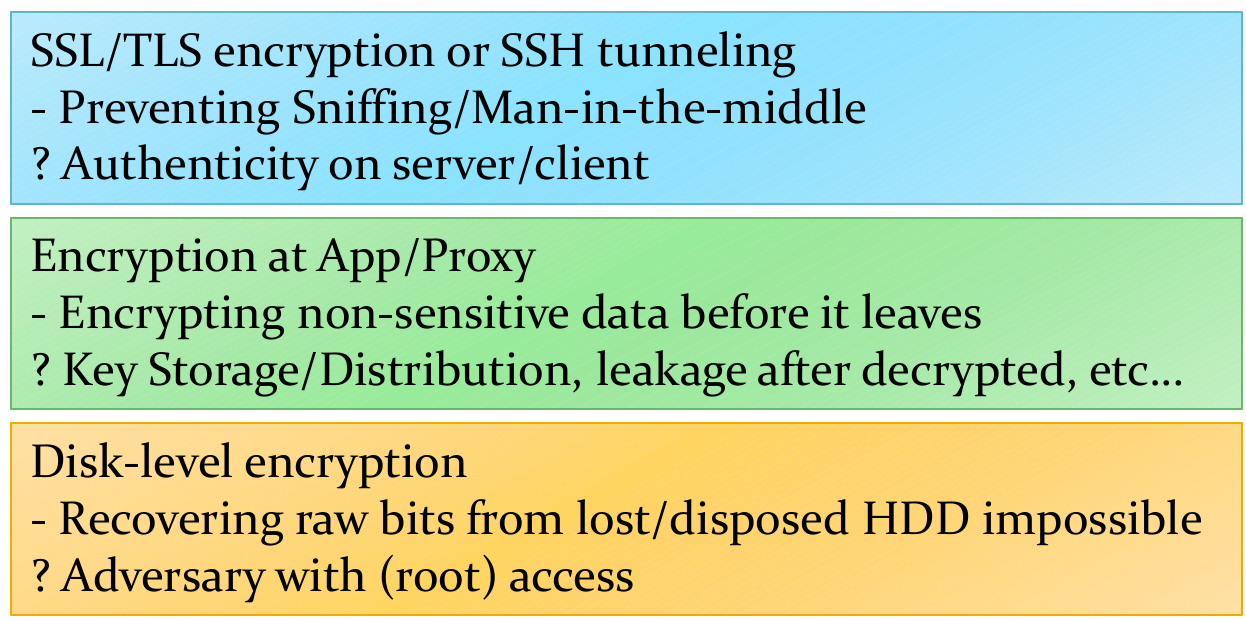
A Taste of Solving Security (1/2)
- Think about outsourcing data to an untrusted DB at Cloud
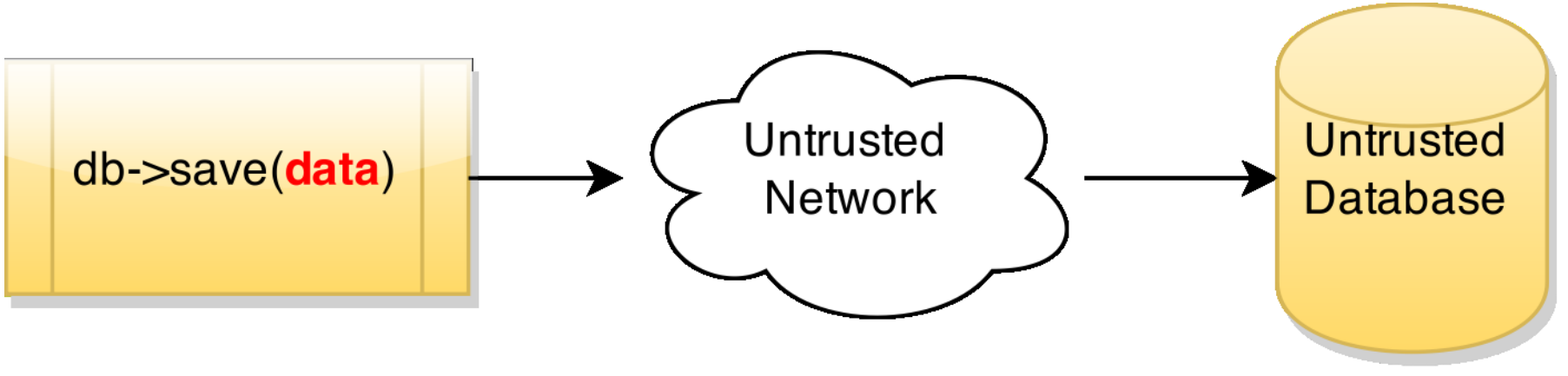
- Intuitively, need encryptions to protect data
- Security goals?
- At rest vs. in transit? What technologies? Pros and Cons?
- Which Security Principles?
- Threat Modeling? Adversary's capabilities
- More: Performance, Usability, Searching over encrypted data?
A Taste of Solving Security (2/2)
- Think about outsourcing data to an untrusted DB at Cloud
- Some security solutions: